IRON - Intelligent Reaction on Network Events is a new research project of the Trust@FHH group. The overall goal is to develop an IF-MAP based security infrastructure for common networks. As part of their bachelor studies at the Fachhochschule Hannover (FHH), 14 students work within this project for two terms.
UPDATE: The project was successfully finished in July 2010. The implementation results (for example irond, our open source IF-MAP 2.0 server) will form the basis for future work.
Introduction
Today’s networks usually compose a large number of different systems, ranging from DHCP servers to security components like Firewalls, VPN Gateways, NAC solutions and Intrusion Detection/Prevention Systems (IDS). While each of those systems has partial information about the network, e.g. the DHCP server knowing which IP addresses are assigned and the IDS knowing what network traffic is taking place, there is currently no standardized way to correlate the information from those single distributed sources.
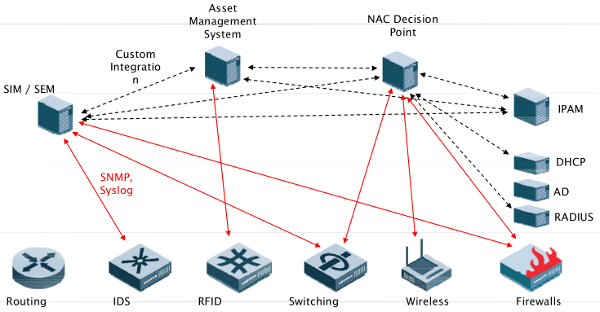
Besides other aspects, at the field of security, this leads to several limitations, e.g.: What happens if an IDS detects suspicious traffic? Normally, it informs the system administrator about the issue, who is then responsible for initiating the appropriate countermeasures (e.g. configuring firewall systems in a way to block the suspicious traffic). If the IDS could talk directly and on its own to the firewall system, the network would be able to respond automatically and immediately to the potential threat. This is just one example that shows the benefits provided by a mechanism that enables a standardized exchange of information reflecting the current status of the network. A promising approach for achieving the described kind of information exchange is proposed within the Trusted Computing Group’s IF-MAP specification. Its goal is to provide a standardized and interoperable way of storing an retrieving metadata about the current status of the network. The specification itself is part of the Trusted Network Connect (TNC) framework - an open standard for Network Access Control (NAC). The communication model of IF-MAP is based upon a publish / search / subscribe paradigm. So called MAP Clients (MAPC) can publish metadata to a MAP Server (MAPS). Furthermore, MAP Clients can retrieve metadata from the MAP Server either by issuing search operations or subscriptions. Search operations look for exisiting metadata and cause an immediate response. By using subscriptions, a MAP Client states to the MAP Server that it is interested in some sort of metadata. As a consequence, the MAP Server notifies the MAP Client about any changes to existing or new metadata that matches the subscription of the client.
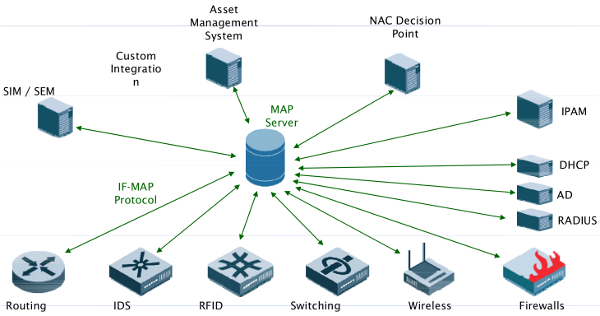
An IF-MAP based infrastructure enables you to get the big picture of your network. When current security tools are extended to support IF-MAP, metadata about the whole network and from products of arbitrary vendors can be gathered, analyzed and therefore used to increase the network’s security level.
Goals of the IRON project
The overall goal of IRON is to develop one MAP Server and arbitrary MAP Clients to investigate the impact that IF-MAP can have on today’s networks. The development is focused on open source software. The basis for the development of the MAP Server is the IF-MAP@FHH implementation. The following open source products will be extended to support IF-MAP:
- tnc@fhh - the open source TNC implementation.
- ISC DHCP - the open source DHCP implementation.
- Nagios - the industry standard in IT infrastructure monitoring.
- Snort - the open source network intrusion prevention and detection system.
- netfilter/iptables - the packet filtering framework inside the Linux 2.4.x and 2.6.x kernel series.
The MAP Clients will publish metadata to and receive metadata from the MAP Server. A primary goal is to develop general use cases for the exchange of metadata between the mentioned systems that mitigate threats that today’s networks have to face (malware infection, data leakage, attacks mounted by internal staff, etc).
General information about IRON
- Type: Research project of bachelor students
- Start: September 2009
- Duration: 2 terms (until July 2010)
- Team: 14 bachelor students, 2 research associates and 1 professor acting as advisors

Hochschule Hannover
University of Applied Sciences and Arts
Faculty IV, Dept. of Computer Science
Ricklinger Stadtweg 120
30459 Hannover, Germany
trust-at-hsh@listserv.dfn.de