Metalyzer and VisITMeta 0.2.0 released
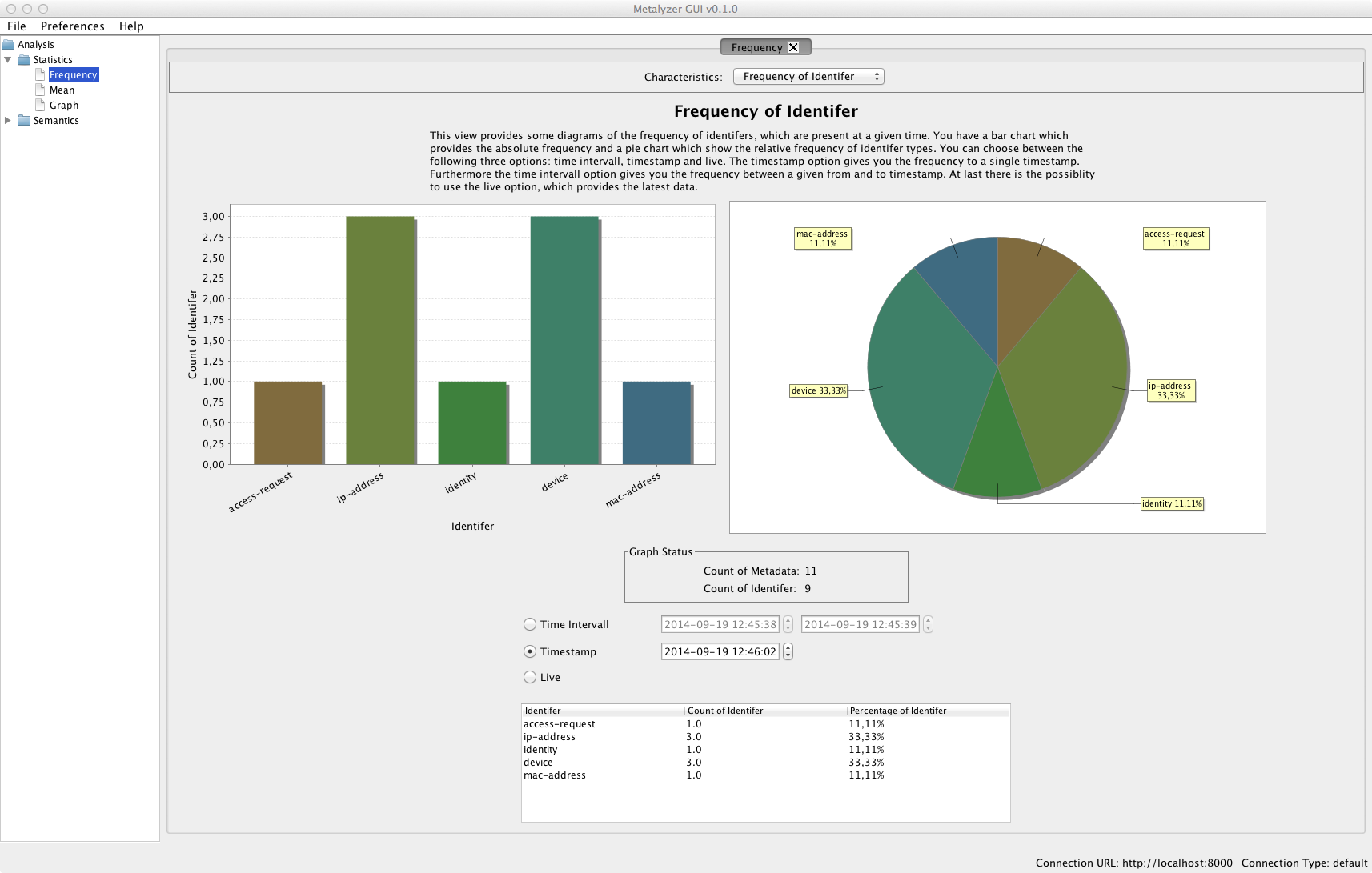
With Metalyzer we introduce a software, that allows to analyse IF-MAP data for statistic and semantic features.
Metalyzer consists of two separate modules:
-
a module that can be loaded by the dataservice application of VisITMeta, that performs the analysis on MAP data and provides REST-like access to the results
-
a visualization client that presents these results via tables, charts and other diagrams.
Some of the analysis that can be done with Metalyzer include the absolute and relative frequencies of different identifiers and metadata or an overview of associated IP addresses and MAC addresses, found by following a given path in the IF-MAP graph data.
The statistic analysis is partly done by using the R framework, whereas the visualization via charts and diagrams uses the JFreechart library.
Metalyzer was developed by a group of 9 students during their bachelor studies within two terms at the Hochschule Hannover.
Please find the sourcecode and instructions on how to build Metalyzer and include it in a VisITMeta runtime environment in the projects Github repository.
In combination with the release of Metalyzer in its first version we also release VisITMeta in version 0.2.0.
The main feature of this version is the added support for external modules - like Metalyzer - , to allow arbitrary processing on the stored MAP data.
We also fixed a bug that happened when the delta is calculated after a single value metadata was updated, and added the possibility to select and unselect single nodes in the GUI application.
The sourcecode of VisITMeta is also available at Github on the projects repository page.
19 Sep 2014
irond now fully supports IF-MAP 2.2
Good news, everyone!
The freshly released 0.5.0 version of our MAP server irond incorporates a number of changes to provide full compliance with the IF-MAP 2.2 specification. Some of the features include (see the specification for the whole changelog):
-
MAP Content Autorization - MAP Content Authorization provides a standard model
for controlling what operations MAP Clients can execute upon the content of a MAP server.
-
ifmap-server identifier - The IF-MAP server-identifier is a well known extended identifier that provides a dedicated identifier on which MAP servers can create server-capability metadata to indicate which capabilities they supports. The IF-MAP server-identifier is published by the MAP server itself to enable MAP clients to find out which IF-MAP version and optional capabilities the MAP server they intend to communicate with supports.
-
ifmap-timestamp-fraction metadata attribute - This special or “operational” attribute that MAP servers add to stored metadata enables for finely grained timestamps with potentially arbitrary precision.
To the best of our knowledge, the Trust@HsH research group are the first to implement a fully IF-MAP 2.2 compliant MAP server and we are proud to provide researchers in industry and academia with an open source implementation to support their research activities.
You can find precompiled binaries and the sources on our github page. Please consult the README for details on building irond on your own.
Note: We already released version 0.5.1 of irond, as we changed a small shortcoming in the build process.
01 Sep 2014
Updates on VisITMeta and irondemo
Just a few days after the last release, we like to introduce VisITMeta 0.1.2 to the public.
Changes and new features include
- Bipartite layout: identifiers and metadata are ordered in 5 columns, where columns 1 and 5 are used by metadata attached to one identifier, column 3 is used by link metadata and columns 2 and 4 are used to show identifiers.
- Dataservice uses neo4j v2.1.2 instead of v1.8
- Extended identifier now uses the root-element of their inner XML to represent them
- Metadata nodes now also allow different textual representation (two supported styles at the moment: just the typename of the metadatum, or with the publish timestamp in a second text line)
- Transparency of glow effects now works correctly
- Fixed a bug that occured when the liveview-checkbox was unchecked too soon after application startup
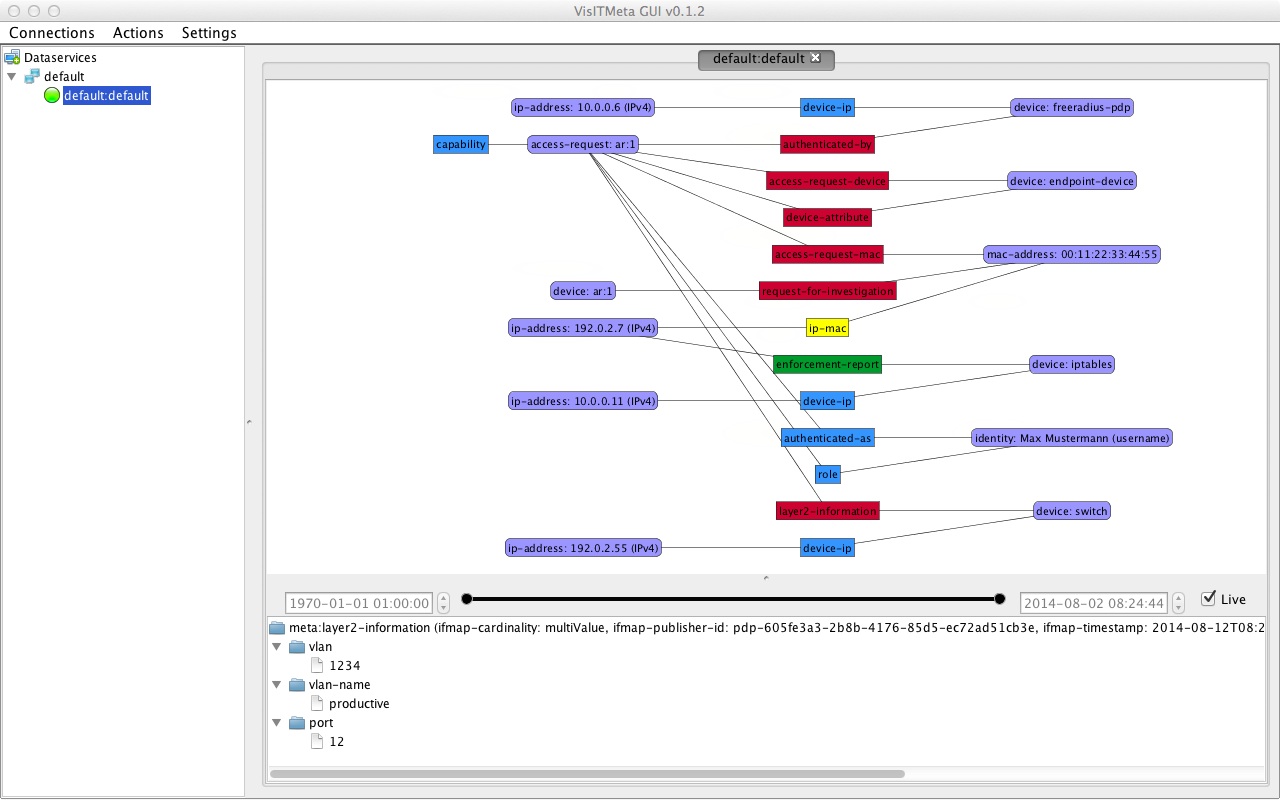 This screenshot shows the new bipartite layout as well as some of the features from version 0.1.1, like enhanced identifier information or the new information panel at the bottom of the GUI.
This screenshot shows the new bipartite layout as well as some of the features from version 0.1.1, like enhanced identifier information or the new information panel at the bottom of the GUI.
Furthermore, we released version 0.4.5 of our demonstration environment irondemo.
It features a new scenario visitmeta-project as well as some bugfixing/enhancements to the agenda parser (now allows trailing/leading whitespace and blank lines).
Both projects are available via their repositories on Github.
12 Aug 2014
VisITMeta 0.1.1 released
We’re proud to announce the release 0.1.1 of our IF-MAP visualisation tool VisITMeta.
Changes and new features (since version 0.0.5) include
- Now using ifmapj v2.2.0.
- Support for external motion control devices; a (simple) integration of the LeapMotion device for control via hand and gesture recognition was also released as a separate project. Check the Readme-file of that project to see how you can build and integrate it within the VisITMeta visualization application.
- Identifer nodes now show more information directly, i.e. IP addresses now state ip-address: 10.0.0.1 (IPv4) instead of just ip-address.
- Identifier nodes can be colored according to their type.
- Further information about identifier and metadata is now shown via a extra subscreen on the bottom instead of a tooltip.
- Fixed a severe bug inside the dataservice application.
06 Aug 2014
ifmapj 2.2.0 released
Today we released version 2.2.0 of our Java library for IF-MAP Clients, ifmapj.
With this version we implement the version 2.2 of the official IF-MAP specification.
Changes and new features include
- Raw XML request and response logging can be turned on by setting a system property.
- A ThreadSafe SSRC for connections.
- Ability to set an initial connection timeout when creating a SSRC.
- AccessRequest identifier: remove deprecation of administrative-domain.
- New metadata wrapper that allows XPath-based queries on metadata documents.
- Add ifmap-timestamp-fraction to Metadata interface.
The new version is also already available via Maven central.
16 Jul 2014
VisITMeta 0.0.5 released
Today we released version 0.0.5 of our IF-MAP visualisation tool VisITMeta.
Changes and new features include
- Support for multiple parallel IF-MAP connections, controllable by REST and GUI (alpha version)
- Create and stop subscriptions via REST interface
- Removed dump functionality
- Configuration files in YAML format, parsing via snakeyaml
- Fixed several bugs within dataservice and visualization
10 Jun 2014
A Change in Leadership
Trust@HsH group founder and former group lead Prof. Dr. Josef von Helden has been elected for the office of president of the University of Applied Sciences and Arts, Hanover and has taken office on May, 12th (see official press release). As a consequence thereof, he unfortunaltey had to resign as the group lead of Trust@HsH.
Luckily, with Prof. Dr. Volker Ahlers, Prof. Dr. Felix Heine and Prof. Dr. Carsten Kleiner as new group lead and Leonard Renners as an additional research associate in the SIMU project, the Trust@HsH is stronger in members than ever before and eager to tackle new scientific challenges.
We wish Prof. Dr. von Helden good fortune for his new assignment and may he lead the univiersity with the same passion, commitment and aptitude that he has built up and managed the Trust@HsH group.
26 May 2014












 This screenshot shows the new bipartite layout as well as some of the features from version 0.1.1, like enhanced identifier information or the new information panel at the bottom of the GUI.
This screenshot shows the new bipartite layout as well as some of the features from version 0.1.1, like enhanced identifier information or the new information panel at the bottom of the GUI.






